IAM Policies and Bucket Policies and ACLs! Oh, My! (Controlling Access to S3 Resources) | AWS Security Blog
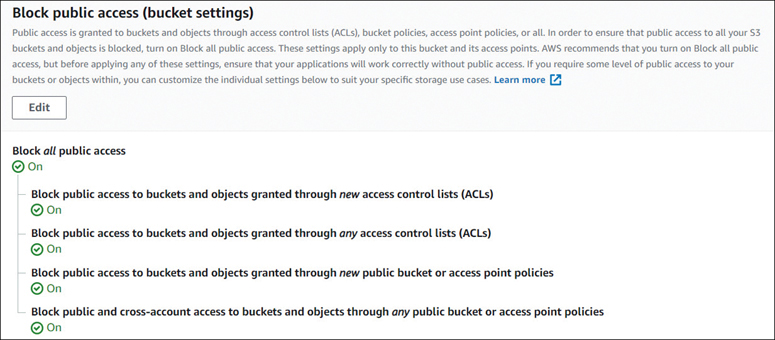
Amazon S3 Bucket Security | Determining Appropriate Data Security Controls | Pearson IT Certification
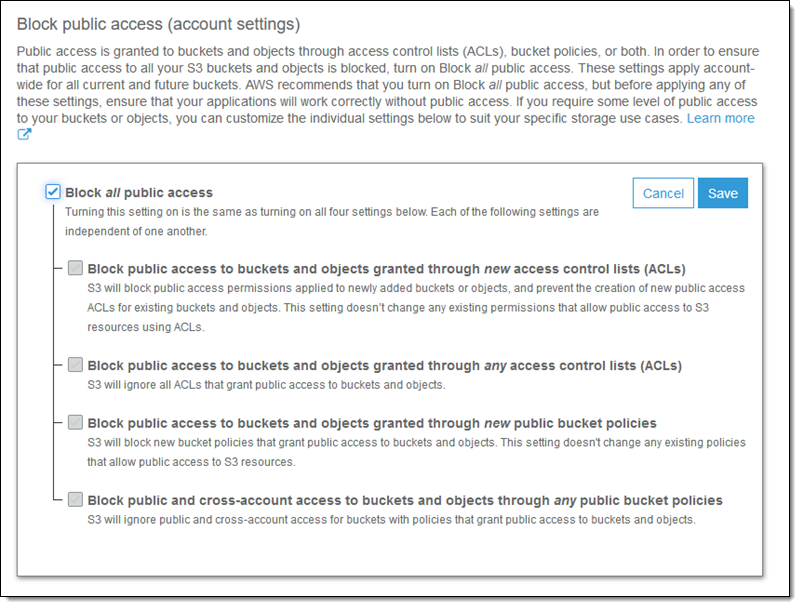
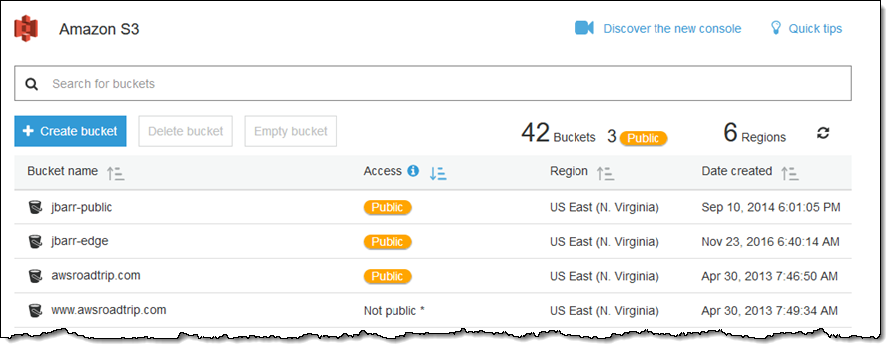
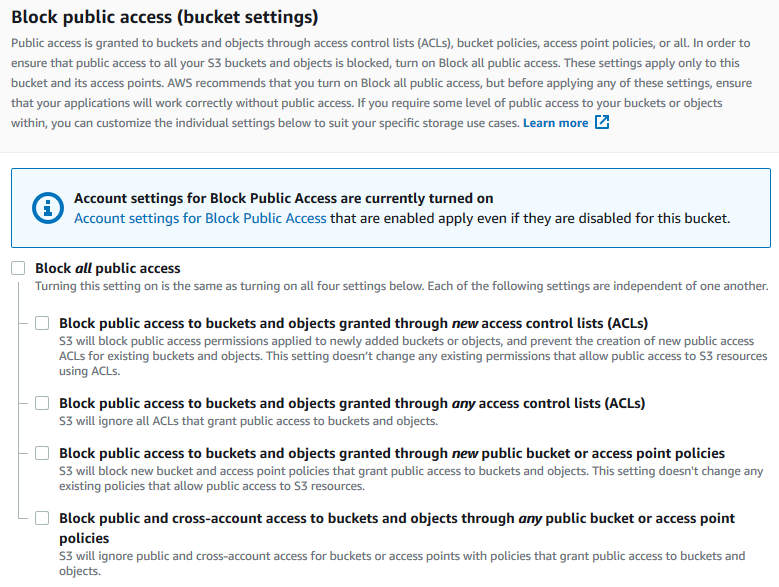
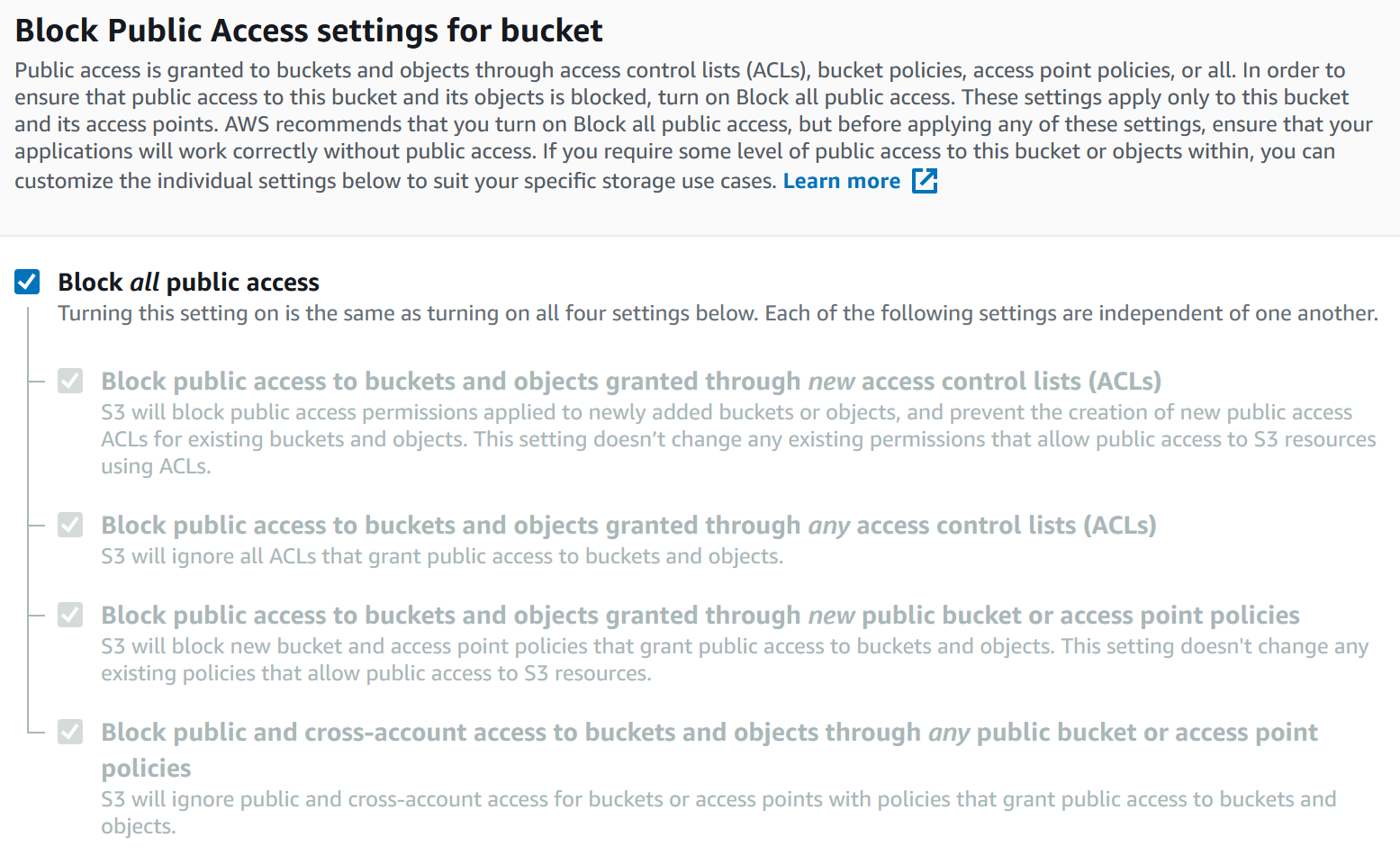
Amazon S3 Block Public Access – Another Layer of Protection for Your Accounts and Buckets | AWS News Blog

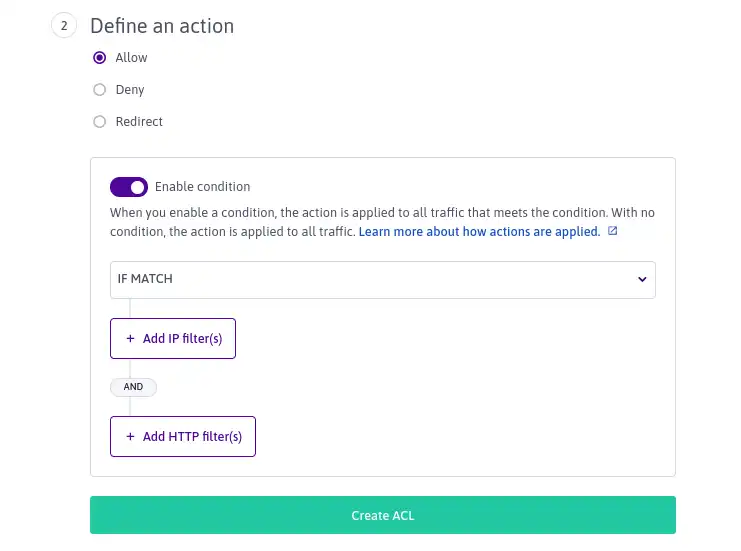
How to Use Bucket Policies and Apply Defense-in-Depth to Help Secure Your Amazon S3 Data | AWS Security Blog

IAM Policies and Bucket Policies and ACLs! Oh, My! (Controlling Access to S3 Resources) | AWS Security Blog

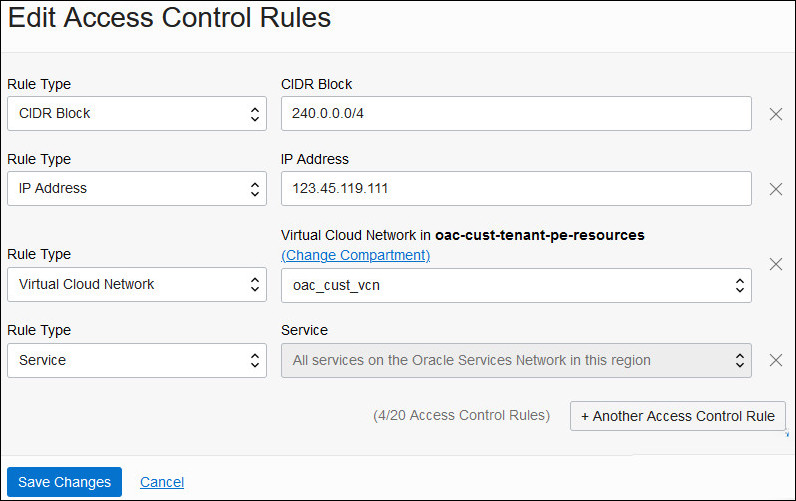
alibaba cloud - How can I restrict access to a file on OSS while still allowing download using wget or curl - Stack Overflow

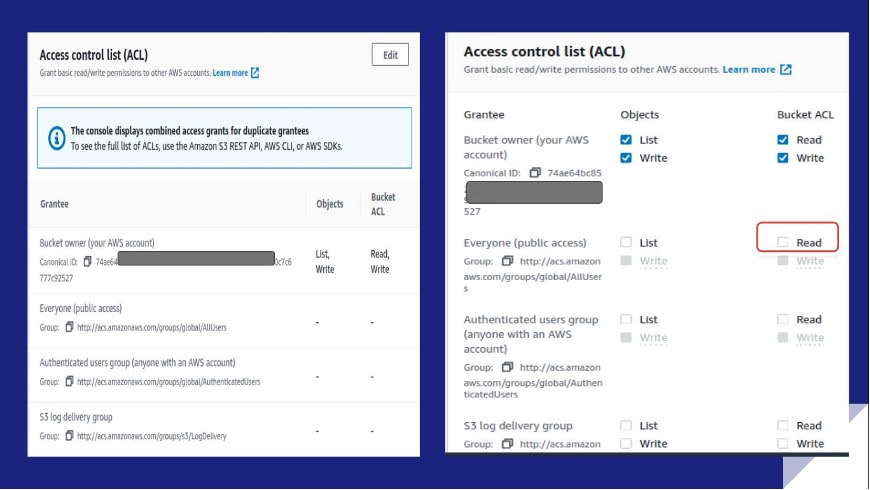
IAM Policies and Bucket Policies and ACLs! Oh, My! (Controlling Access to S3 Resources) | AWS Security Blog
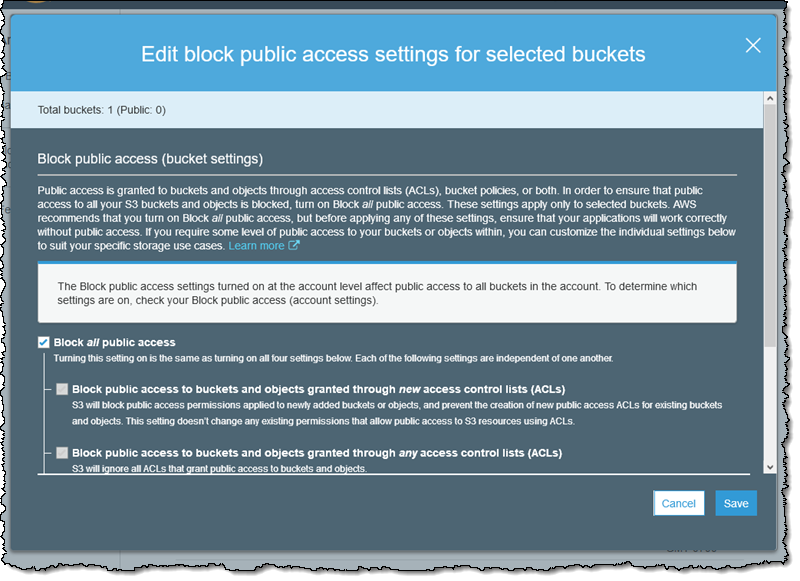
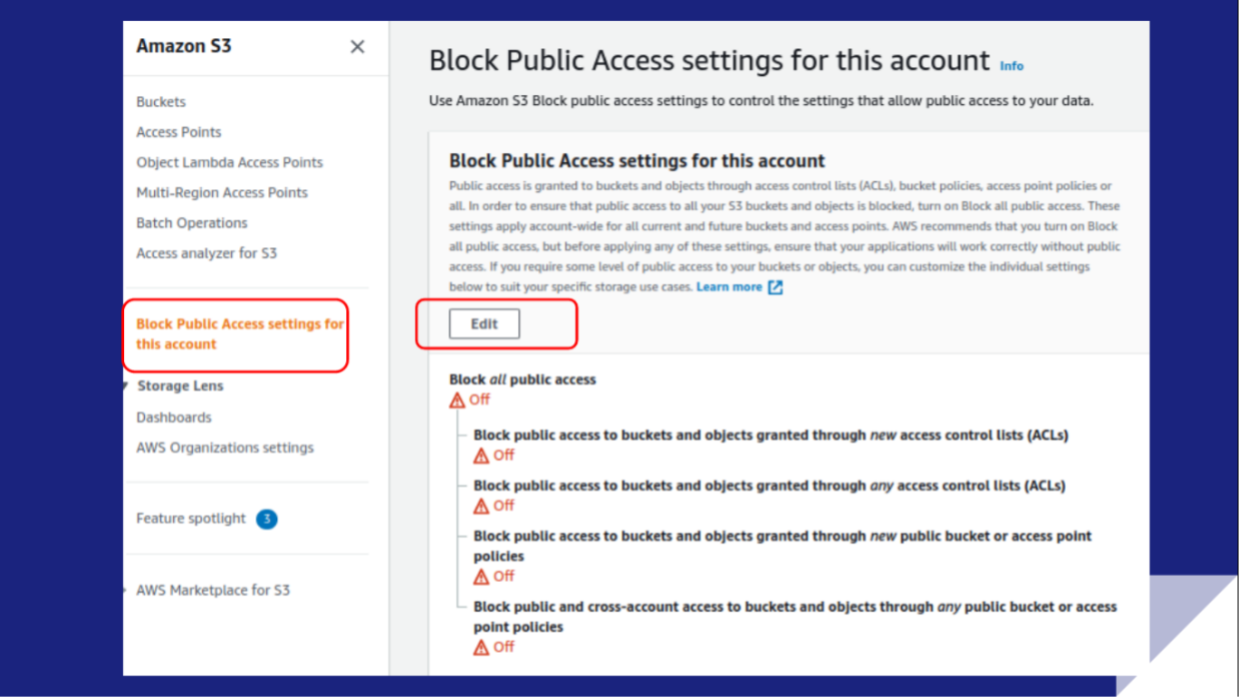
Amazon S3 Block Public Access – Another Layer of Protection for Your Accounts and Buckets | AWS News Blog

amazon web services - What combination of Block Public Access settings makes my s3 bucket viewable to everyone? - Stack Overflow